Penetration Testing
What is Penetration Testing?
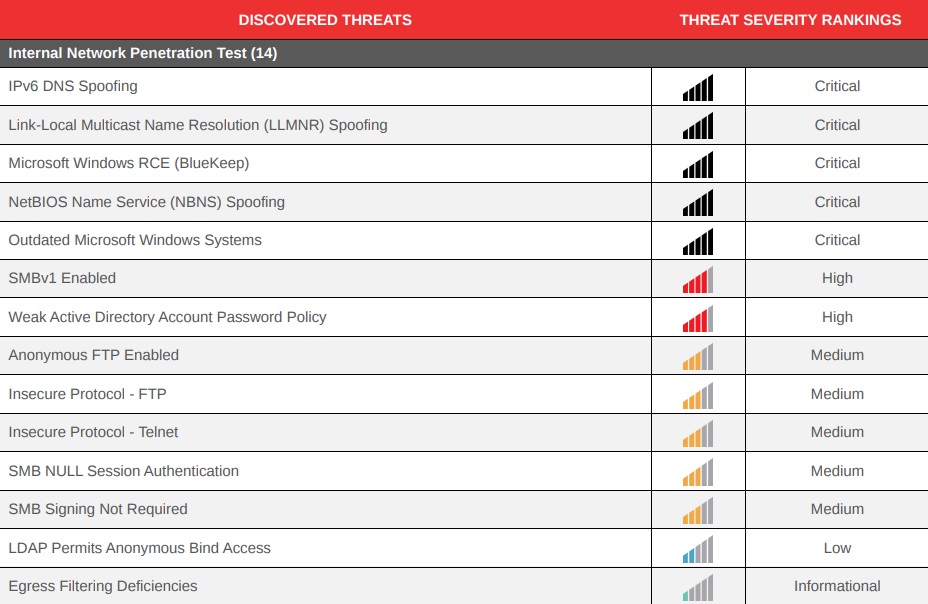
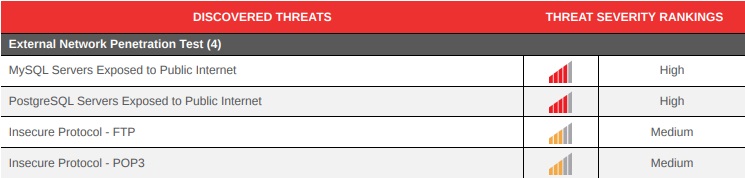
Penetration testing, also known as ethical hacking or security testing, is a simulated cyberattack designed to evaluate your system’s defenses. Our penetration testing experts use industry-leading methodologies, including black-box, white-box, and gray-box penetration testing, to uncover security weaknesses and recommend actionable solutions.
Comprehensive Penetration Testing Services for Robust Cybersecurity
In today’s digital landscape, cyber threats are constantly evolving. At On-Site Technology, we provide expert penetration testing services to help businesses identify vulnerabilities before attackers exploit them. Our team of certified ethical hackers performs in-depth penetration testing to assess your network, applications, and IT infrastructure against real-world cyber threats.